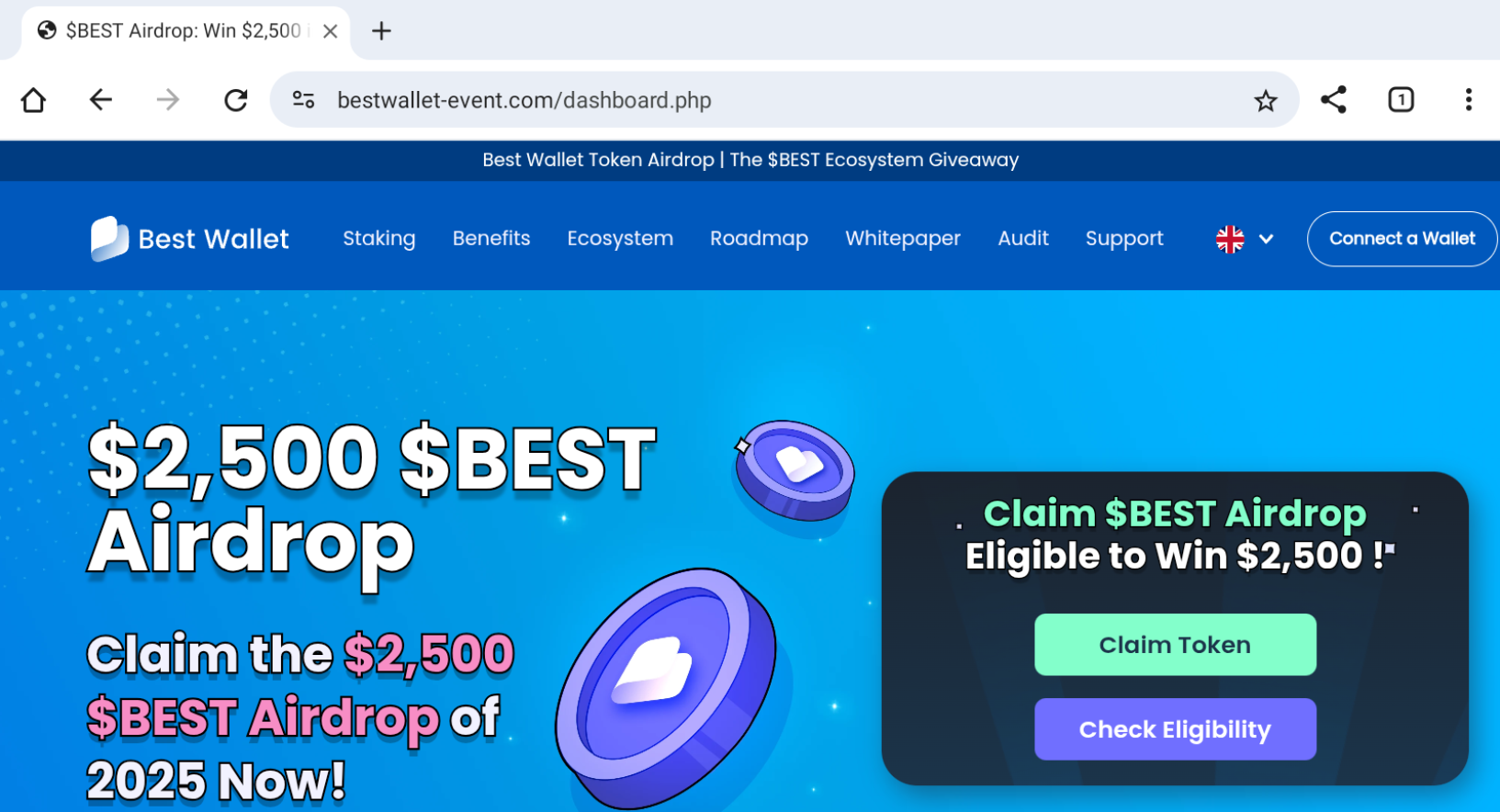
Apple has raised concerns about a new Texas state law, SB 2420, which introduces age assurance requirements for app stores and app developers.
One of its main objections is that the requirements are over the top and don’t take into account what the user is actually trying to do. Apple stated:
“We are concerned that SB2420 impacts the privacy of users by requiring the collection of sensitive, personally identifiable information to download any app, even if a user simply wants to check the weather or sports scores.”
Starting January 1, 2026, anyone creating a new Apple account will need to confirm they’re over 18. Users under 18 will have to join a Family Sharing group and get parental consent to download or buy apps, or make in-app purchases.
With age verification comes the requirement for companies to collect, store, and manage sensitive documents or data points (such as government IDs or parental authority details). The more of this data that’s stored, the greater the consequences if it’s breached.
Apple’s pushback against SB2420 is an explicit call to consider the inherent privacy risks of increased age verification mandates. It argues the requirement should only apply to apps and services where age checks are genuinely needed.
Adding to the complexity, individual states are making their own laws to protect minors online, but all using different methods of implementation. Apple reportedly warned developers that similar laws will take effect in Utah and Louisiana later in the year, so they should be prepared.
Discord’s data breach highlights the risks of age verification
An illustration of Apple’s concerns was the recent third-party breach at a customer support provider for Discord. Discord stated that cybercriminals targeted a firm that helped to verify the ages of its users. Discord did not name the company involved, but has revoked the provider’s access to the system that was targeted in the breach.
The compromise exposed sensitive government ID images for around 70,000 users who submitted age-verification data. The criminals claim to have stolen the data of 5.5 million unique users from the company’s Zendesk support system instance, including government IDs and partial payment information for some people.
We agree with Apple that regulators should be aware of the risks that come with implementing different sets of requirements. We don’t want to see regulatory pressure to collect sensitive information lead to the kind of breaches that everyone’s afraid of.
When sensitive information like government ID photos, full names, and contact details are exposed in a breach, criminals gain powerful tools for identity theft. With access to these details, a fraudster can impersonate someone to access their bank accounts, open new credit lines, or make major purchases in their name. Access to government-issued IDs enables attackers to create convincing fake documents, pass verification checks at financial institutions, and sell authentic-looking identities on the dark web to other criminals. The resulting identity theft can cause victims long-term financial and personal damage.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.