In December 2024, CPAP Medical Supplies and Services Inc. (CPAP), a Jacksonville—a Florida-based provider of sleep therapy services and CPAP machines—experienced a cybersecurity incident that compromised the personal data of over 90,000 patients.
Since CPAP Medical specializes in tailored sleep apnea equipment for the US military, most of the patients are military members, veterans, and their families.
An unauthorized actor accessed CPAP’s network between December 13 and December 21, 2024. The breach wasn’t discovered until late June 2025, and affected parties were notified by mid-August. The stolen data includes:
- Full names
- Birth dates
- Social Security numbers
- Health insurance information
- Medical history
- Treatment plans
The impact is particularly severe for military personnel and their families, many of whom rely on medical equipment and services like those CPAP provides. Exposure of personal and health data can have serious consequences, including risks to personal security, eligibility for benefits, future job applications, and trust in healthcare providers.
CPAP says it is unaware of any misuse of patient data as a result of the incident, but the affected individuals have been offered free credit monitoring and identity theft protection as a precaution.
Healthcare data breaches are unfortunately common, often affecting tens or even hundreds of thousands of people each year. Cybercriminals frequently target healthcare organizations because of the sensitive data they store—information that can be exploited for identity theft, fraud, or blackmail.
Protecting yourself after a data breach
CPAP has sent personalized notifications to the affected patients. If you think you have been the victim of a data breach, here are steps you can take to protect yourself:
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened and follow any specific advice it offers.
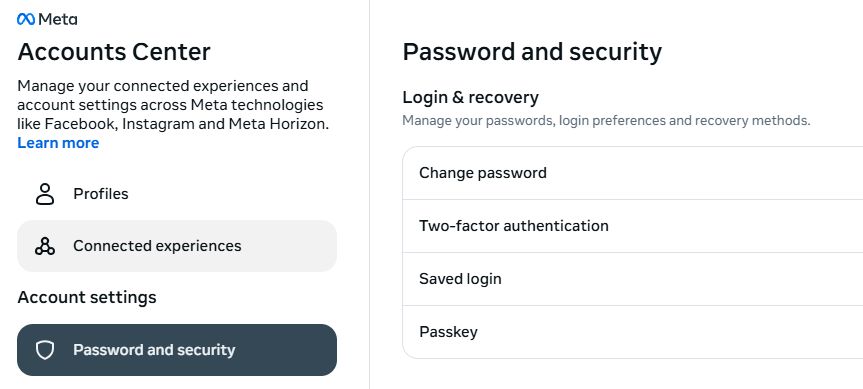
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop, or phone as your second factor. Some forms of 2FA can be phished just as easily as a password, but 2FA that relies on a FIDO2 device can’t be phished.
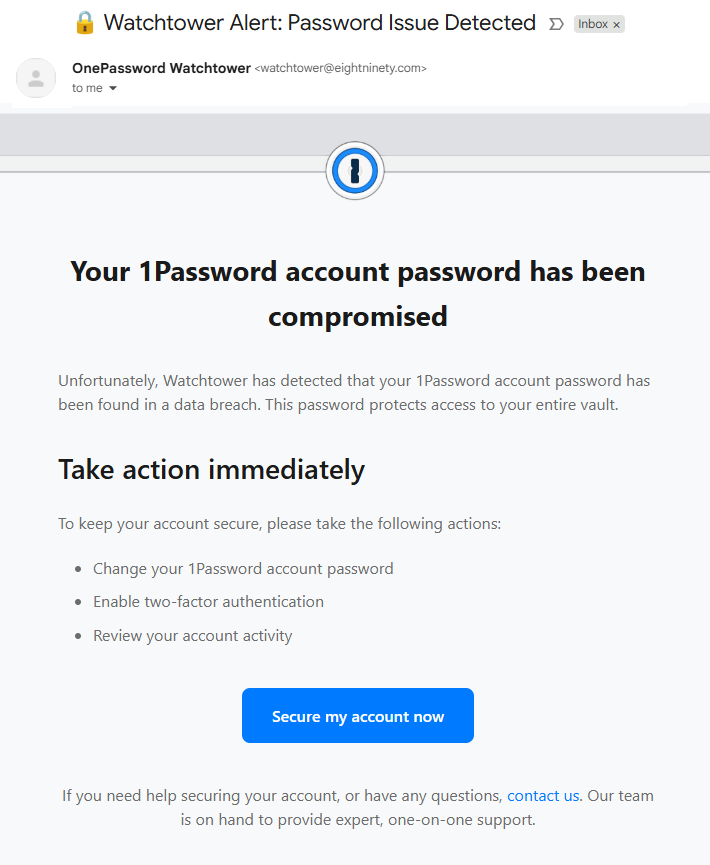
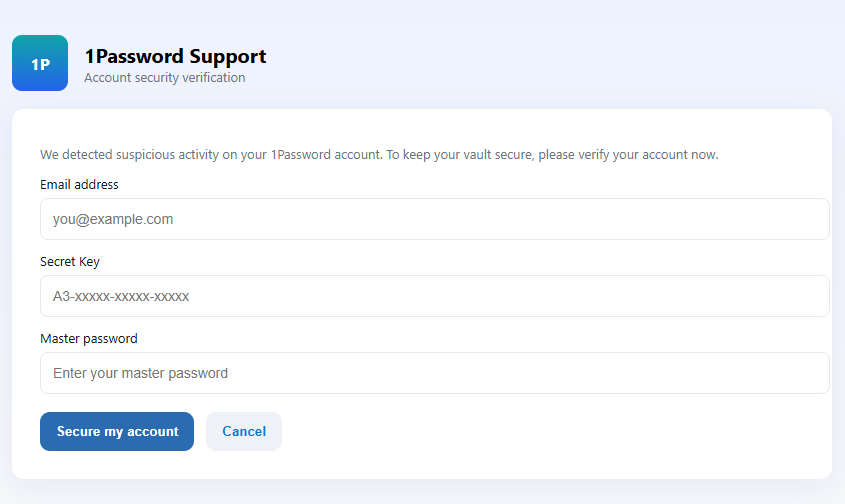
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the company’s website to see if it’s contacting victims and verify the identity of anyone who contacts you using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Consider not storing your card details. It’s definitely more convenient to let sites remember your card details, but we highly recommend not storing that information on websites.
- Set up identity monitoring, which alerts you if your personal information is found being traded illegally online and helps you recover after.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.