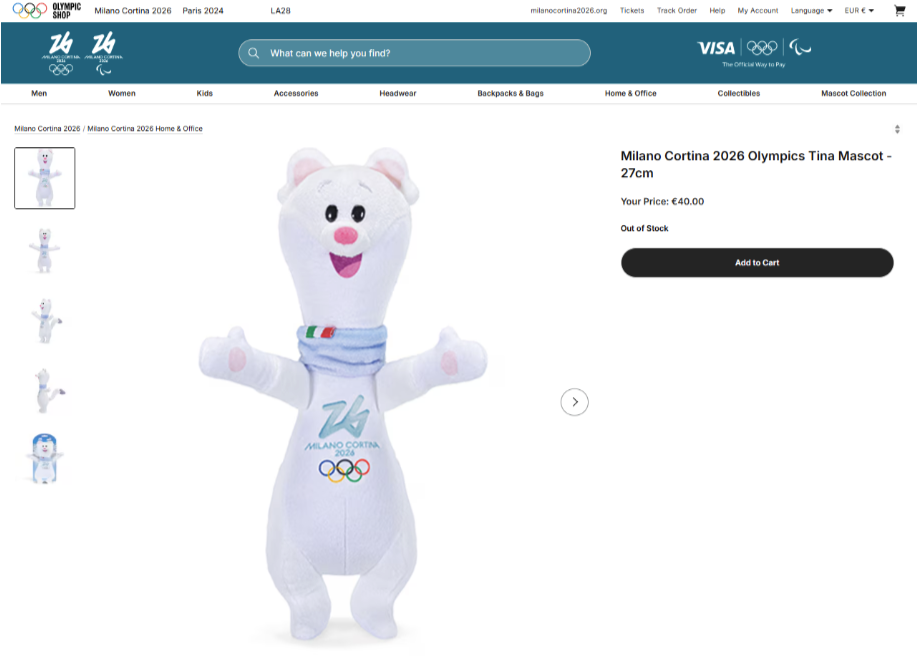
If you’ve seen the two stoat siblings serving as official mascots of the Milano Cortina 2026 Winter Olympics, you already know Tina and Milo are irresistible.
Designed by Italian schoolchildren and chosen from more than 1,600 entries in a public poll, the duo has already captured hearts worldwide. So much so that the official 27 cm Tina plush toy on the official Olympics web shop is listed at €40 and currently marked out of stock.
Tina and Milo are in huge demand, and scammers have noticed.
When supply runs out, scam sites rush in
In roughly the past week alone, we’ve identified nearly 20 lookalike domains designed to imitate the official Olympic merchandise store.
These aren’t crude copies thrown together overnight. The sites use the same polished storefront template, complete with promotional videos and background music designed to mirror the official shop.olympics.com experience.

The layout and product pages are the same—the only thing that changes is the domain name. At a quick glance, most people wouldn’t notice anything unusual.
Here’s a sample of the domains we’ve been tracking:
2026winterdeals[.]top
olympics-save[.]top
olympics2026[.]top
postolympicsale[.]com
sale-olympics[.]top
shopolympics-eu[.]top
winter0lympicsstore[.]top (note the zero replacing the letter “o”)
winterolympics[.]top
2026olympics[.]shop
olympics-2026[.]shop
olympics-2026[.]top
olympics-eu[.]top
olympics-hot[.]shop
olympics-hot[.]top
olympics-sale[.]shop
olympics-sale[.]top
olympics-top[.]shop
olympics2026[.]store
olympics2026[.]top
Based on telemetry, additional registrations are actively emerging.
Reports show users checking these domains from multiple regions including Ireland, the Czech Republic, the United States, Italy, and China—suggesting this is a global campaign targeting fans worldwide.
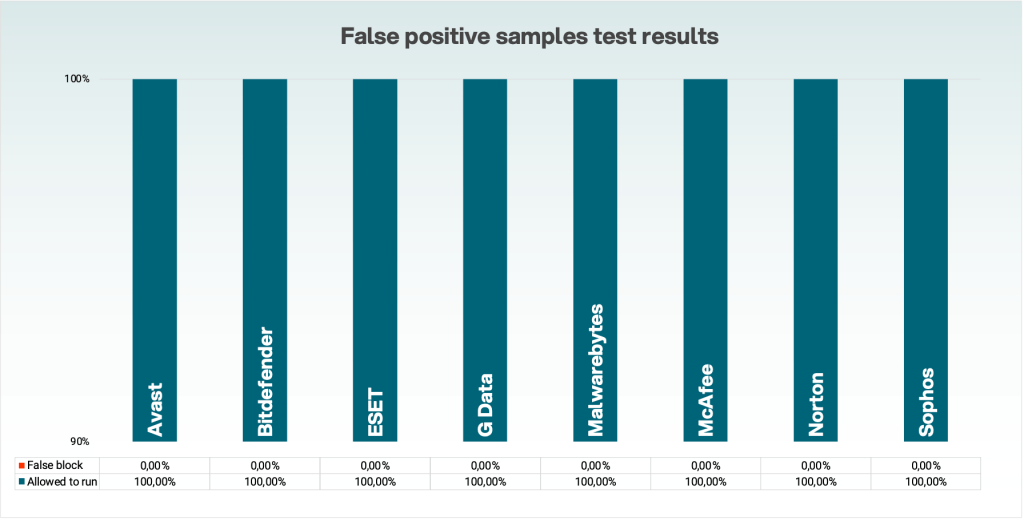
Malwarebytes blocks these domains as scams.
Anatomy of a fake Olympic shop
The fake sites are practically identical. Each one loads the same storefront, with the same layout, product pages, and promotional banners.
That’s usually a sign the scammers are using a ready-made template and copying it across multiple domains. One obvious giveaway, however, is the pricing.
On the official store, the Tina plush costs €40 and is currently out of stock. On the fake sites, it suddenly reappears at a hugely discounted price—in one case €20, with banners shouting “UP & SAVE 80%.” When an item is sold out everywhere official and a random .top domain has it for half price, you’re looking at bait.
The goal of these sites typically includes:
- Stealing payment card details entered at checkout
- Harvesting personal information such as names, addresses, and phone numbers
- Sending follow-up phishing emails
- Delivering malware through fake order confirmations or “tracking” links
- Taking your money and shipping nothing at all
The Olympics are a scammer’s playground
This isn’t the first time cybercriminals have piggybacked on Olympic fever. Fake ticket sites proliferated as far back as the Beijing 2008 Games. During Paris 2024, analysts observed significant spikes in Olympics-themed phishing and DDoS activity.
The formula is simple. Take a globally recognized brand, add urgency and emotional appeal (who doesn’t want an adorable stoat plush for their kid?), mix in limited availability, and serve it up on a convincing-looking website. With over 3 billion viewers expected for Milano Cortina, the pool of potential victims is enormous.
Scammers are getting smarter. AI-powered tools now let them generate convincing phishing pages in multiple languages at scale. The days of spotting a scam by its broken images and multiple typos are fading fast.
Protect yourself from Winter Olympics scams
As excitement builds ahead of the Winter Olympics in Milano Cortina, expect scammers to ramp up their efforts across fake shops, fraudulent ticket sites, bogus livestreams, and social media phishing campaigns.
- Buy only from shop.olympics.com. Type the address directly into your browser and bookmark it. Don’t click links from ads or emails.
- Don’t trust extreme discounts. If it’s sold out officially but “50–80% off” elsewhere, it’s likely a scam.
- Check the domain closely. Watch for odd extensions like .top or .shop, extra hyphens, or letter swaps like “winter0lympicsstore.”
- Never enter payment details on unfamiliar sites. If something feels off, leave immediately.
- Use browser protection. Tools like Malwarebytes Browser Guard block known scam sites in real time, for free. Scam Guard can help you check suspicious websites before you buy.
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!