Vulnerable Facebook Messenger and WhatsApp users are getting more protection thanks to a move from the applications’ owner, Meta. The company has announced more safeguards to protect users (especially the elderly) from scammers.
The social media, publishing, and VR giant has added a new warning on WhatsApp that displays an alert when you share your screen during video calls with unknown contacts.
On Messenger, protection begins with on-device behavioral analysis, complemented by an optional cloud-based AI review that requires user consent. The on-device protection will flag suspicious messages from unknown accounts automatically. You then have the option to forward it to the cloud for further analysis (although note that this will likely break the default end-to-end encryption on that message, as Meta has to read it to understand the content). Meta’s AI service will then explain why the device interpreted the message as risky and what to do about it, offering information about common scams to provide context.
That context will be useful for vulnerable users, and it comes after Meta worked with researchers at social media analysis company Graphika to document online scam trends. Some of the scams it found included fake home remodeling services, and fraudulent government debt relief sites, both targeting seniors. There were also fake money recovery services offering to get scam victims’ funds back (which we’ve covered before).
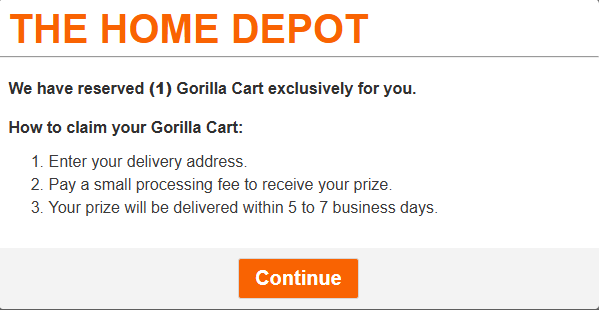
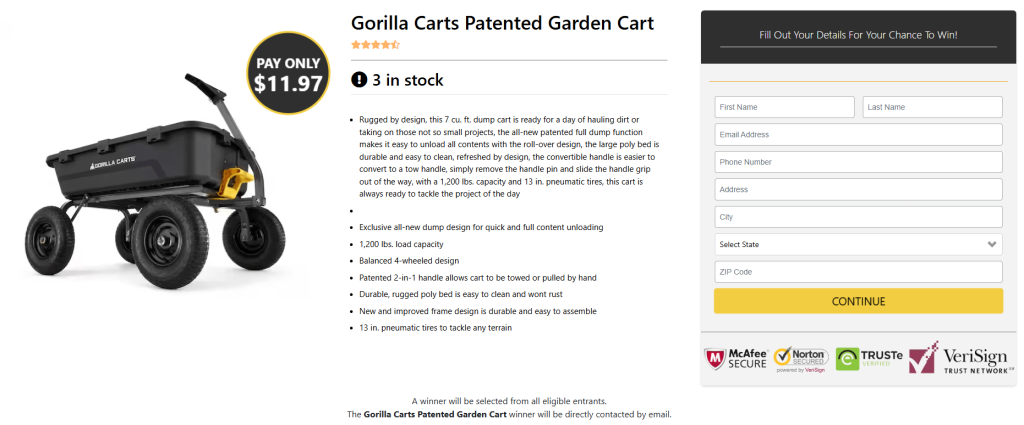
Here’s a particularly sneaky scam that Meta identified: fake customer support scammers. These jerks monitor comments made under legitimate online accounts for airlines, travel agencies, and banks. They then contact the people who commented, impersonating customer support staff and persuading them to enter into direct message conversations or fill out Google Forms. Meta has removed over 21,000 Facebook pages impersonating customer support, it said.
A rising tide of scams
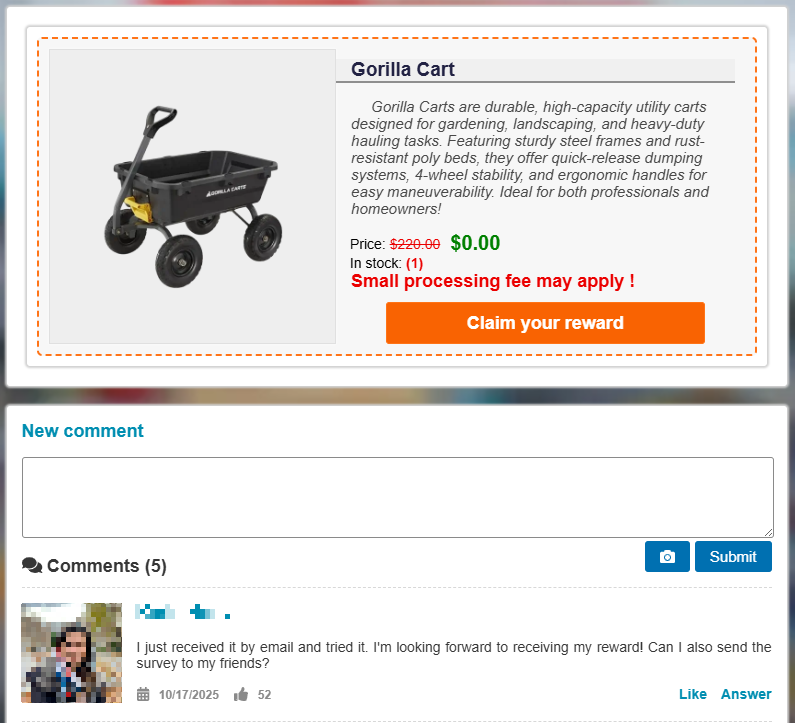
We can never have too many protections for vulnerable internet users, as scams continue to target them through messaging and social media apps. While scams target everyone (costing Americans $16.6 billion in losses, according to the FBI’s cybercrime unit IC3), those over 60 are hit especially hard. They lost $4.8 billion in 2024. Overall, losses from scams were up 33% across the board year-on-year.
Other common scams include “celebrity baiting”, which uses celebrity figures without their knowledge to dupe users into fraudulent schemes including investments and cryptocurrency. With deepfakes making it easier than ever to impersonate famous people, Meta has been testing facial recognition to help spot celebrity-bait ads for a year now, and recently announced plans to expand that initiative.
If you know someone less tech-savvy who uses Meta’s apps, encourage them to try these new protections—like Passkeys and Security Checkup. Passkeys let you log in using a fingerprint, face, or PIN, while Security Checkup guides you through steps to secure your account.
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!