Google has released an update for its Chrome browser that includes two security fixes. Both are classified as high severity, and one is reportedly exploited in the wild. These flaws were found in Chrome’s V8 engine, which is the part of Chrome (and other Chromium-based browsers) that runs JavaScript.
Chrome is by far the world’s most popular browser, used by an estimated 3.4 billion people. That scale means when Chrome has a security flaw, billions of users are potentially exposed until they update.
These vulnerabilities are serious because they affect the code that runs almost every website you visit. Every time you load a page, your browser executes JavaScript from all sorts of sources, whether you notice it or not. Without proper safety checks, attackers can sneak in malicious instructions that your browser then runs—sometimes without you clicking anything. That could lead to stolen data, malware infections, or even a full system compromise.
That’s why it’s important to install these patches promptly. Staying unpatched means you could be open to an attack just by browsing the web, and attackers often exploit these kinds of flaws before most users have a chance to update. Always let your browser update itself, and don’t delay restarting to apply security patches, because updates often fix exactly this kind of risk.
How to update
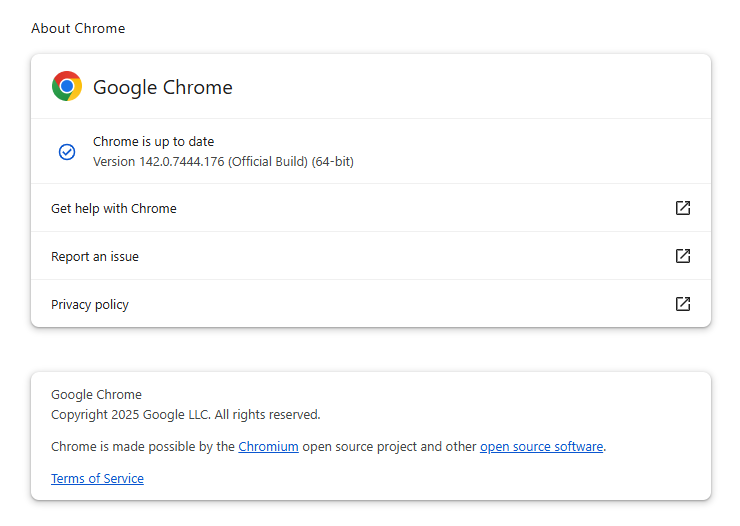
The Chrome update brings the version number to 142.0.7444.175/.176 for Windows, 142.0.7444.176 for macOS and 142.0.7444.175 for Linux. So, if your Chrome is on the version number 142.0.7444.175 or later, it’s protected from these vulnerabilities.
The easiest way to update is to allow Chrome to update automatically, but you can end up lagging behind if you never close your browser or if something goes wrong—such as an extension stopping you from updating the browser.
To update manually, click the “More” menu (three stacked dots), then choose Settings > About Chrome. If there is an update available, Chrome will notify you and start downloading it. Then relaunch Chrome to complete the update, and you’ll be protected against these vulnerabilities.
You can find more detailed update instructions and how to read the version number in our article on how to update Chrome on every operating system.
Technical details
Both vulnerabilities are characterized as “type confusion” flaws in V8.
Type confusion happens when code doesn’t verify the object type it’s handling and then uses it incorrectly. In other words, the software mistakes one type of data for another—like treating a list as a single value or a number as text. This can cause Chrome to behave unpredictably and, in some cases, let attackers manipulate memory and execute code remotely through crafted JavaScript on a malicious or compromised website.
The actively exploited vulnerability—Google says “an exploit for CVE-2025-13223 exists in the wild”—was discovered by Google’s Threat Analysis Group (TAG). It can allow a remote attacker to exploit heap corruption via a malicious HTML page. Which means just visiting the “wrong” website might be enough to compromise your browser.
Google hasn’t shared details yet about who is exploiting the flaw, how they do it in real-world attacks, or who’s being targeted. However, the TAG team typically focuses on spyware and nation-state attackers that abuse zero days for espionage.
The second vulnerability, tracked as CVE-2025-13224, was discovered by Google’s Big Sleep, an AI-driven project to discover vulnerabilities. It has the same potential impact as the other vulnerability, but cybercriminals probably haven’t yet figured out how to use it.
Users of other Chromium-based browsers—like Edge, Opera, and Brave—can expect similar updates in the near future.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.


![Be careful responding to unexpected job interviews 6 Malwarebytes blocks meetingzs[.]com](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/11/meetingzscomblock.png)