A short while ago, our friends at Malwaretips wrote about a text scam impersonating Robinhood, a popular US-based investment app that lets people trade stocks and cryptocurrencies. The scam warns users about supposed “suspicious activity” on their accounts.
As if to demonstrate that this phishing campaign is still very much alive, one of our employees received one of those texts.
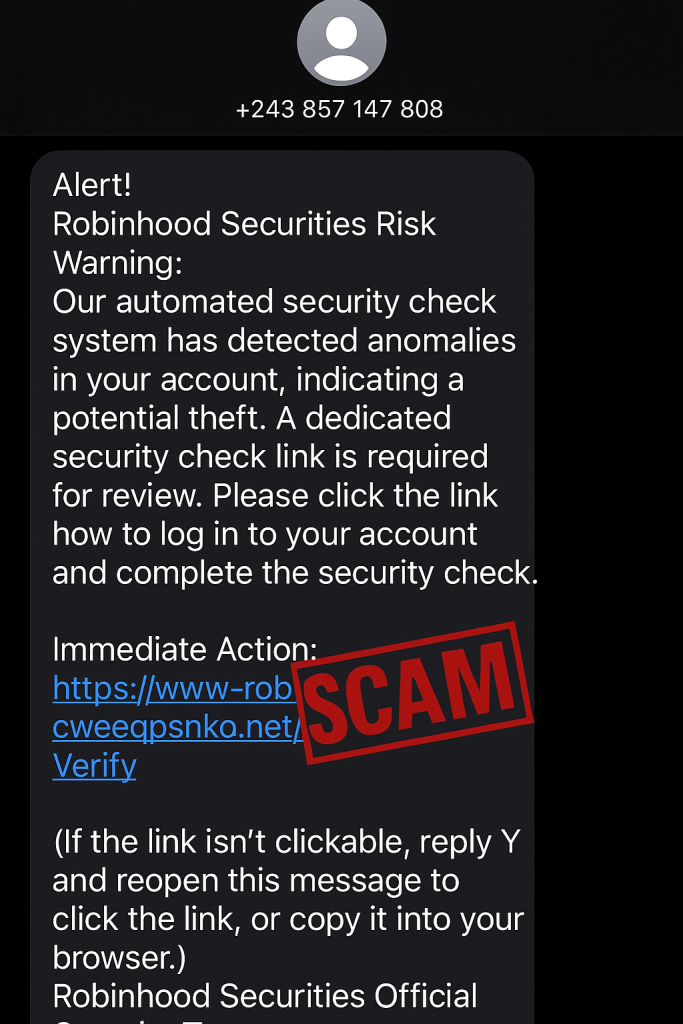
“Alert!
Robinhood Securities Risk Warning:
Our automated security check system has detected anomalies in your account, indicating a potential theft. A dedicated security check link is required for review. Please click the link below to log in to your account and complete the security check.
Immediate Action: https://www-robinhood.cweegpsnko[.]net/Verify
(If the link isn’t clickable, reply Y and reopen this message to click the link, or copy it into your browser.)
Robinhood Securities Official Security Team”
As usual, we see some red flags:
- Foreign number: The country code +243 belongs to the Democratic Republic of the Congo, not the US, where the real Robinhood is based.
- Urgency: The phrase “Immediate Action” is designed to pressure you.
- Fake domain: The URL that tries to look like the legitimate robinhood.com website.
- Reply: The instructions to reply “Y” if a link isn’t clickable are a common phishing tactic.
But if the target follows the instructions to visit the link, they would find a reasonably convincing copy of Robinhood’s login page. It wouldn’t be automatically localized like the real one, but nobody in the US would know the difference. Logging in there hands the scammers your Robinhood login credentials and allows them to clean out your account.
According to Malwaretips, some of the fake websites even redirected you to the legitimate site after showing the “verification complete” message.
They also warned that some scammers will try to harvest additional personal data from the account, including:
- Tax documents
- Full name
- Social Security Number (if on file)
- Bank account information
How to stay safe
What to do if you receive texts like these
The best tip to stay safe is to make sure you’re aware of the latest scam tactics. Since you’re reading our blog, you’re off to a good start.
- Never reply to or follow links in unsolicited tax refund texts, calls, or emails, even if they look urgent.
- Never share your Social Security number or banking details with anyone claiming to process your tax refund.
- Go direct. If in doubt, contact the company through official channels.
- Use an up-to-date real-time anti-malware solution, preferably with a web protection component.
Pro tip: Did you know that you can submit suspicious messages like these to Malwarebytes Scam Guard, which instantly flags known scams?
What to do if you clicked the phishing link
- Change your Robinhood password
- Enable two-factor authentication (2FA) if you haven’t already.
- Contact Robinhood support through the official support channels.
- Report the scam to Robinhood and other relevant authorities.
Indicators of compromise (IOCs)
www-robinhood.cweegpsnko[.]net
www-robinhood.fflroyalty[.]com
robinhood-securelogin[.]com
robinhood-verification[.]net
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.