Fresh off a breathless Super Bowl Sunday, we’re less thrilled to bring you this week’s Weirdo Wednesday. Two stories caught our eye, both involving men who crossed clear lines and invaded women’s privacy online.
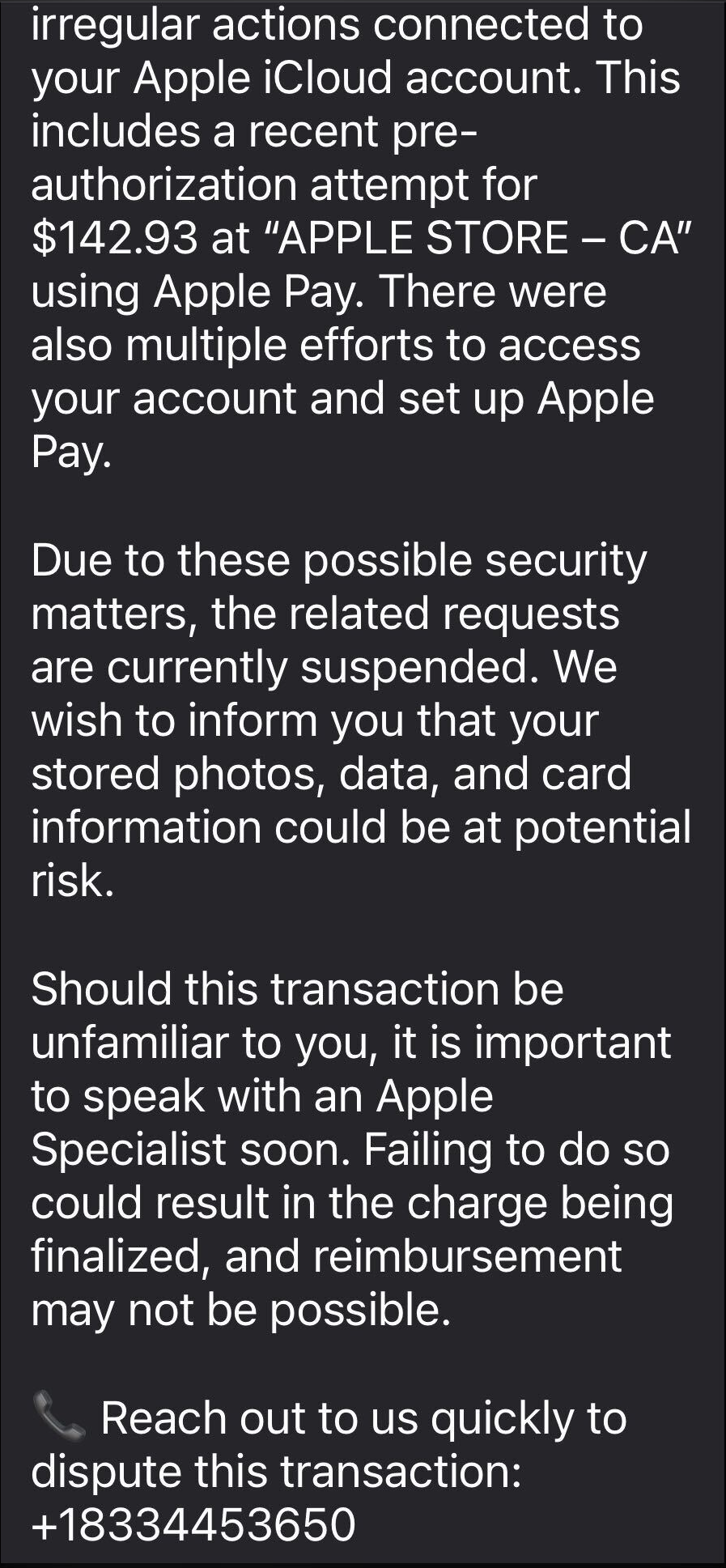
Last week, 27-year-old Kyle Svara of Oswego, Illinois admitted to hacking women’s Snapchat accounts across the US. Between May 2020 and February 2021, Svara harvested account security codes from 571 victims, leading to confirmed unauthorized access to at least 59 accounts.
Rather than attempting to break Snapchat’s robust encryption protocols, Svara targeted the account owners themselves with social engineering.
After gathering phone numbers and email addresses, he triggered Snapchat’s legitimate login process, which sent six-digit security codes directly to victims’ devices. Posing as Snapchat support, he then sent more than 4,500 anonymous messages via a VoIP texting service, claiming the codes were needed to “verify” or “secure” the account.
Svara showed particular interest in Snapchat’s My Eyes Only feature—a secondary four-digit PIN meant to protect a user’s most sensitive content. By persuading victims to share both codes, he bypassed two layers of security without touching a single line of code. He walked away with private material, including nude images.
Svara didn’t do this solely for his own kicks. He marketed himself as a hacker-for-hire, advertising on platforms like Reddit and offering access to specific accounts in exchange for money or trades.
Selling his services to others was how he got found out. Although Svara stopped hacking in early 2021, his legal day of reckoning followed the 2024 sentencing of one of his customers: Steve Waithe, a former track and field coach who worked at several high-profile universities including Northeastern. Waithe paid Svara to target student athletes he was supposed to mentor.
Svara also went after women in his home area of Plainfield, Illinois, and as far away as Colby College in Maine.
He now faces charges including identity theft, wire fraud, computer fraud, and making false statements to law enforcement about child sex abuse material. Sentencing is scheduled for May 18.
How to protect your Snapchat account
Never send someone your login details or secret codes, even if you think you know them.
This is also a good time to talk about passkeys.
Passkeys let you sign in without a password, but unlike multi-factor authentication, passkeys are cryptographically tied to your device, and can’t be phished or forwarded like one-time codes. Snapchat supports them, and they offer stronger protection than traditional multi-factor authentication, which is increasingly susceptible to smart phishing attacks.
Bad guys with smart glasses
Unfortunately, hacking women’s social media accounts to steal private content isn’t new. But predators will always find a way to use smart tech in nefarious ways. Such is the case with new generations of ‘smart glasses’ powered by AI.
This week, CNN published stories from women who believed they were having private, flirtatious interactions with strangers—only to later discover the men were recording them using camera-equipped smart glasses and posting the footage online.
These clips are often packaged as “rizz” videos—short for “charisma”—where so-called manfluencers film themselves chatting up women in public, without consent, to build followings and sell “coaching” services.
The glasses, sold by companies like Meta, are supposed to be used for recording only with consent, and often display a light to show that they’re recording. In practice, that indicator is easy to hide.
When combined with AI-powered services to identify people, as researchers did in 2024, the possibilities become even more chilling. We’re unaware of any related cases coming to court, but suspect it’s only a matter of time.
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!