Researchers have discovered a large ad fraud campaign on Google Play Store.
The Satori Threat Intelligence and Research team found 224 malicious apps which were downloaded over 38 million times and generated up to 2.3 billion ad requests per day. They named the campaign “SlopAds.”
Ad fraud is a type of fraud that lets advertisers pay for ads even though the number of impressions (the times that the ad has been seen) is enormously exaggerated.
While the main victims of ad fraud are the advertisers, there are consequences for the users that had these apps installed as well, such as slowed-down devices and connections due to the apps executing their malicious activity in the background without the user even being aware.
At first, to stay under the radar of Google’s app review process and security software, the downloaded app will behave as advertised, if a user has installed it directly from the Play Store.
But if the installation has been initiated by one of the campaign’s ads, the user will receive some extra files in the form of a steganographically encrypted payload.
If the app passes the first check it will receive four .png images that, when decrypted and reassembled, are actually an .apk file. The malicious file uses WebView (essentially a very basic browser) to send collected device and browser information to a Control & Command (C2) server which determines, based on that information, what domains to visit in further hidden WebViews.
The researchers found evidence of an AI (Artificial Intelligence) tool training on the same domain as the C2 server (ad2[.]cc). It is unclear whether this tool actively managed the ad fraud campaign.
Based on similarities in the C2 domain, the researchers found over 300 related domains promoting SlopAds-associated apps, suggesting that the collection of 224 SlopAds-associated apps was only the beginning.
Google removed all of the identified apps listed in this report from Google Play. Users are automatically protected by Google Play Protect, which warns users and blocks apps known to exhibit SlopAds associated behavior at install time on certified Android devices, even when apps come from sources outside of the Play Store.
You can find a complete list of the removed apps here: SlopAds app list
How to avoid installing malicious apps
While the official Google Play Store is the safest place to get your apps from, there is no guarantee that it will remain a non-malicious app just because it is in the Google Play Store. So here are a few extra measures you can take:
- Always check what permissions an app is requesting, and don’t just trust an app because it’s in the official Play Store. Ask questions such as: Do the permissions make sense for what the app is supposed to do? Why did necessary permissions change after an update? Do these changes make sense?
- Occasionally go over your installed apps and remove any you no longer need.
- Make sure you have the latest available updates for your device, and all your important apps (banking, security, etc.)
- Protect your Android with security software. Your phone needs it just as much as your computer.
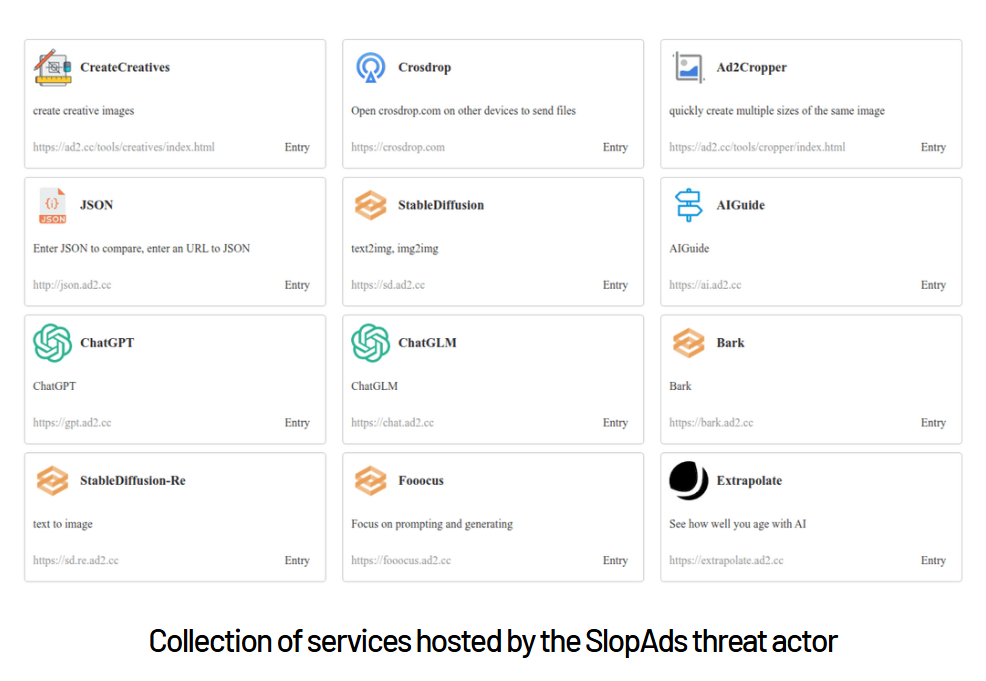
Another precaution you can take if you’re looking for an app, do your research about the app before you go to the app store. As you can see from the screenshot above, many of the apps are made to look exactly the same as very popular legitimate ones (e.g. ChatGPT).
So, it’s important to know in advance who the official developer is of the app you want and if it’s even available from the app store.
As researcher Jim Nielsen demonstrated for the Mac App Store, there are a lot of apps trying to look like ChatGPT, but they are not the real thing. ChatGPT is not even in the Mac App Store, it is available in the Google Play Store for Android, but make sure to check that OpenAI is listed as the developer.
We don’t just report on phone security—we provide it
Cybersecurity risks should never spread beyond a headline. Keep threats off your mobile devices by downloading Malwarebytes for iOS, and Malwarebytes for Android today.