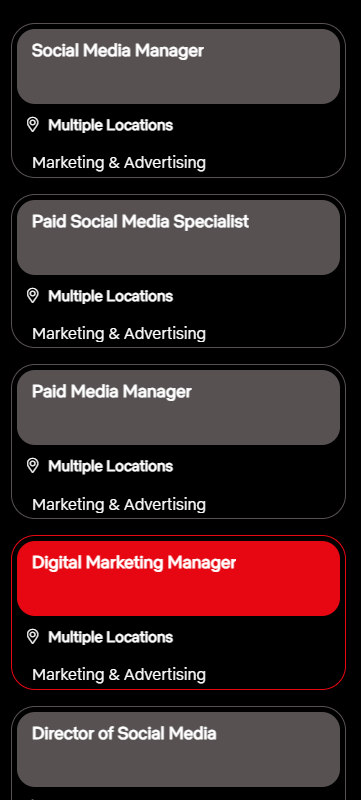
The Computer Emergency Response Team (CERT) for Italy’s “Agenzia per l’Italia Digitale” (AGID) issued a warning that cybercriminals are selling stolen identity documents from hotels operating in Italy.
This summer, a criminal hacker group named “mydocs” infiltrated the booking systems of at least ten Italian hotels, stealing high-resolution scans of ID documents, including passports and national ID cards, provided by guests during check-in. These documents, amounting to tens of thousands in number (potentially up to 100,000), have been offered for sale on dark web forums at prices ranging from $1000 to $10,000. Both Italian and foreign guests are affected, with luxury and city hotels among the breached venues.
While the incident appears to have taken place in June and July of this year, it is not clear how many years back the hotels’ scans are retained for, so you could be at risk if you have visited the hotels at an earlier time. AGID did not mention the hotels by name, but we hope the hotels will take it upon themselves to warn the people whose ID information may be for sale.
AGID warns that warned that the stolen data could be used for:
- Fraudulent creation of new documents.
- Opening bank accounts or lines of credit.
- Social engineering attacks against individuals and their contacts.
- Digital identity theft, with serious legal and financial implications.
Authorities advise guests to contact the hotels where they stayed if they suspect their data was compromised and to stay alert for scams or phishing attempts using their information.
Protecting yourself after a data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened and follow any specific advice they offer.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the vendor website to see if they are contacting victims and verify the identity of anyone who contacts you using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Consider not storing your card details. It’s definitely more convenient to get sites to remember your card details for you, but we highly recommend not storing that information on websites.
- Set up identity monitoring. Identity monitoring alerts you if your personal information is found being traded illegally online and helps you recover after.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.

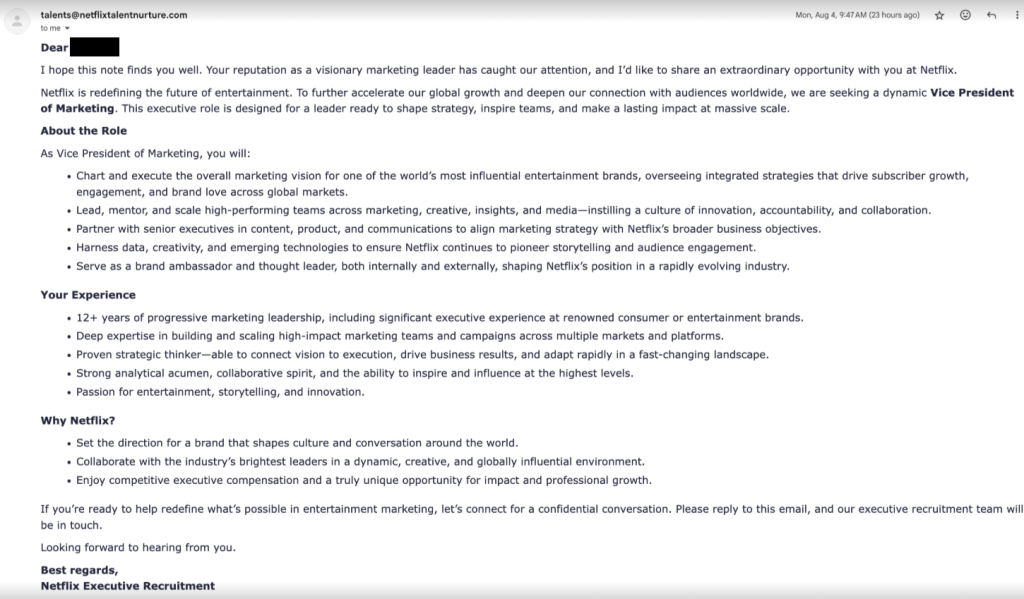
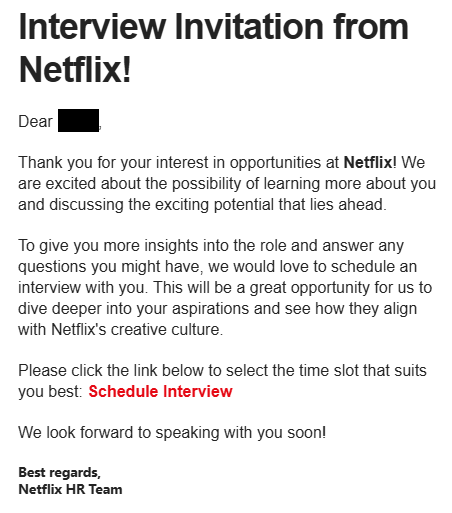
![Netflix scammers target jobseekers to trick them into handing over their Facebook logins 3 Malwarebytes blocks hiring.growwithusnetflx[.]com](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/08/growwithusnetflixcomblock.png)