Last week on Malwarebytes Labs:
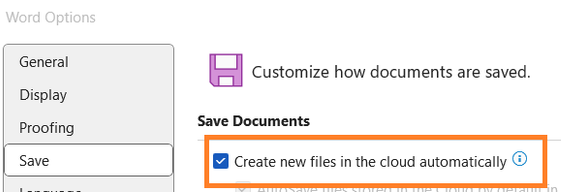
- Microsoft wants to automatically save your Word docs to the cloud
- “No place in our networks”: FCC hangs up on thousands of voice operators in robocall war
- Claude AI chatbot abused to launch “cybercrime spree”
- Developer verification: a promised lift for Android security
- More vulnerable stalkerware victims’ data exposed in new TheTruthSpy flaw
- 77 malicious apps removed from Google Play Store
- AI browsers could leave users penniless: A prompt injection warning
- How a scam hunter got scammed (Lock and Code S06E17)
Stay safe!
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.