A new infostealer called DigitStealer is going after Mac users. It avoids detection, skips older devices, and steals files, passwords, and browser data. We break down what it does and how to protect your Mac.
Researchers have described a new malware called DigitStealer that steals sensitive information from macOS users.
This variant comes with advanced detection-evasion techniques and a multi-stage attack chain. Most infostealers go after the same types of data and use similar methods to get it, but DigitStealer is different enough to warrant attention.
A few things make it stand out: platform-specific targeting, fileless operation, and anti-analysis techniques. Together, they pose relatively new challenges for Mac users.
The attack starts with a file disguised as a utility app called “DynamicLake,” which is hosted on a fake website rather than the legitimate company’s site. To trick users, it instructs you to drag a file into Terminal, which will initiate the download and installation of DigitStealer.
If your system matches certain regions or is a virtual machine, the malware won’t run. That’s likely to hinder analysis by researchers and to steer clear of infecting people in its home country, which is enough in some countries to stay out of prison. It also limits itself to devices with newer ARM features introduced with M2 chips or later. chips, skipping older Macs, Intel-based chips, and most virtual machines.
The attack chain is largely fileless so it won’t leave many traces behind on an affected machine. Unlike file-based attacks that execute the payload in the hard drive, fileless attacks execute the payload in Random Access Memory (RAM). Running malicious code directly in the memory instead of the hard drive has several advantages for attackers:
- Evasion of traditional security measures: Fileless attacks bypass antivirus software and file-signature detection, making them harder to identify using conventional security tools.
- Harder to remediate: Since fileless attacks don’t create files, they can be more challenging to remove once detected. This can make it extra tricky for forensics to trace an attack back to the source and restore the system to a secure state.
DigitStealer’s initial payload asks for your password and tries to steal documents, notes, and files. If successful, it uploads them to the attackers’ servers.
The second stage of the attack goes after browser information from Chrome, Brave, Edge, Firefox and others, as well as keychain passwords, crypto wallets, VPN configurations (specifically OpenVPN and Tunnelblick), and Telegram sessions.
How to protect your Mac
DigitStealer shows how Mac malware keeps evolving. It’s different from other infostealers, splitting its attack into stages, targeting new Mac hardware, and leaving barely any trace.
But you can still protect yourself:
- Use an up-to-date real-time anti-malware solution. DigitStealer highlights the need for advanced behavioral protection, not just signature scans. Malwarebytes for Mac detects DigitStealer as MacOA.Stealer.DigitSteal.
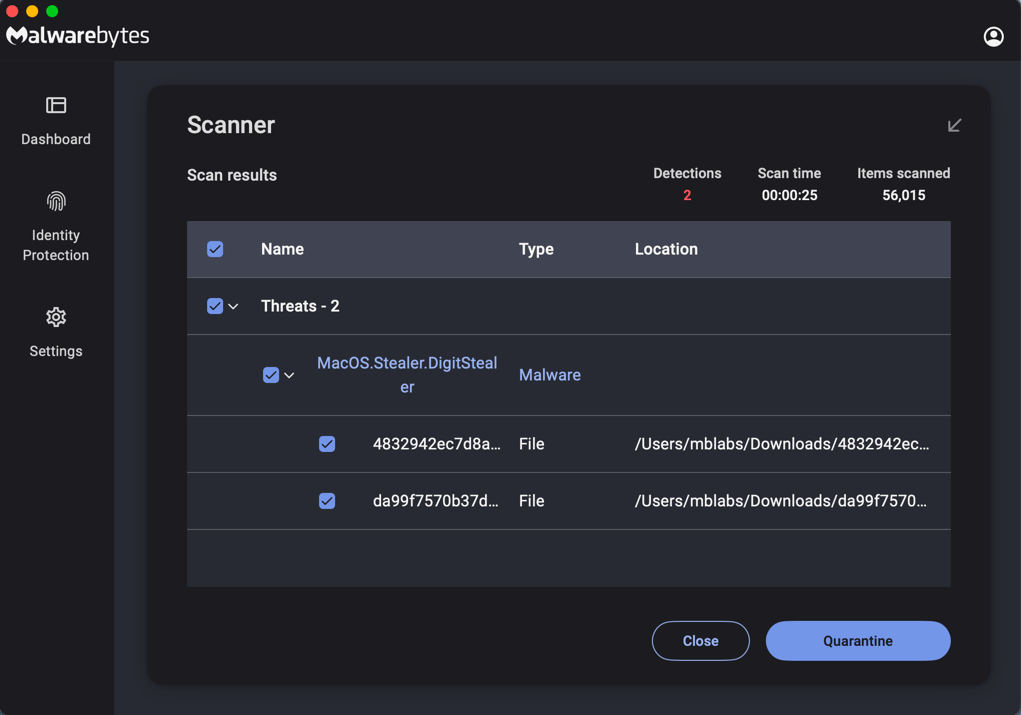
- Always be careful what you run in Terminal. Don’t follow instructions from unsolicited messages.
- Be careful where you download apps from.
- Keep your software, especially your operating system and your security defenses, up to date.
- Turn on multi-factor authentication so a stolen password isn’t enough to break into your accounts.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.


![Be careful responding to unexpected job interviews 9 Malwarebytes blocks meetingzs[.]com](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/11/meetingzscomblock.png)