Cybercriminals are spoofing “email delivery” notifications to look like they came from spam filters inside your own organization. The goal is to lure you to a phishing site that steals login credentials—credentials that could unlock your email, cloud storage or other personal accounts.
The email claims that, due to an upgrade in the Secure Message system, some pending messages didn’t make it to your inbox and are ready to be moved there now.

“Email Delivery Reports: Incoming Pending Messages
We have recently upgraded our Secure Message system, and there are pending messages that have not been delivered to your Inbox.
Failure Delivery Messages
Email Delivery Reports For info@seychellesapartment.com
Status : Subject: Date: Time:
{A couple of message titles that are very generic and common as not to raise any suspicion}
Move To Inbox (button)
Note : The messages will be delivered within 1-2 hours after you receive a confirmation Mail Notice. If this message lands in your spam folder, please move it to your inbox folder
Mail Encrypted by {spoofed domain} © All Rights Reserved. | If you do not wish to receive this message Unsubscribe. (link)”
Both the “Move to Inbox” button and the unsubscribe link abuse a cbssports[.]com redirect to reach the real phishing site located on the domain mdbgo[.]io, which was blocked by Malwarebytes.
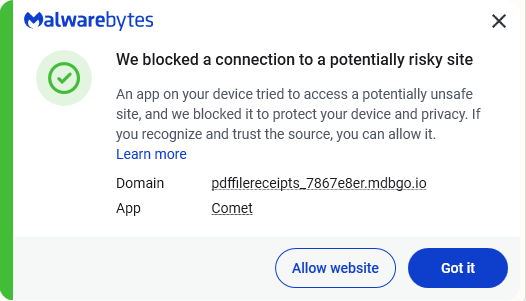
Researchers at Unit42 warned about this type of phishing campaign, so we decided to take a closer look.
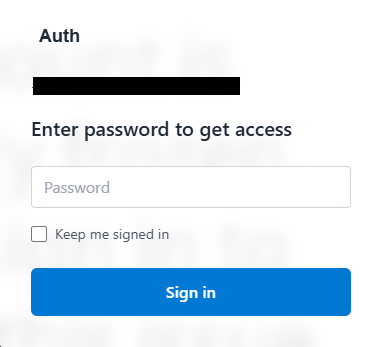
The links pass the spoofed email address as a base64-encoded string to the phishing site. Going to that site, we were served this fake login screen with the target’s domain already filled in—making it look personalized and legitimate:
Contrary to Unit42’s findings, we found that this version of the attack is more sophisticated and likely evolving quickly. The phishing site’s code is heavily obfuscated, and credentials are harvested through a websocket.
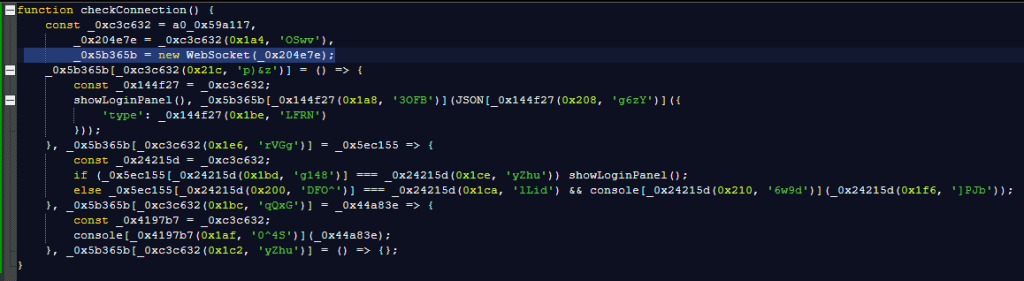
A websocket keeps an open channel between your browser and the website’s server—like a phone call that never hangs up. This lets the browser and server send messages instantly back and forth, in both directions, without needing to reload the page. Cybercriminals love using websockets because they receive your details the instant you type them into a phishing site, and can even send prompts for additional information, such as two-factor authentication (2FA) codes.
This means that if you enter your email and password on such a site, attackers could instantly take control of your email, access cloud-stored files, reset other passwords, and impersonate you across services.
How to stay safe from phishing emails
In phishing attempts like these, two simple rules can save you from lots of trouble.
- Don’t open unsolicited attachments
- Always check the website address in the browser before signing in. Make sure it matches the site you expect to be on.
Other important tips to stay safe from phishing in general:
- Verify the sender. Always check if the sender’s email address matches what you would expect it to be. It’s not always conclusive, but it can help you spot some attempts.
- Double-check requests through another channel if you receive an attachment or a link you weren’t expecting.
- Use up-to-date security software, preferably with a web protection component.
- Keep your device and all its software updated.
- Use multi-factor authentication (MFA) for every account you can.
- Use a password manager. Password managers will not auto-fill a password to a fake site, even if it looks like the real deal to you.
If you already entered credentials on a page you don’t trust, change your passwords immediately.
Pro tip: The free Malwarebytes Browser Guard extension would have stopped this attack as well:
![Phishing emails disguised as spam filter alerts are stealing logins 5 Malwarebytes Browser Guard blocks the subdomain of mdbgo[.]io](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/11/mdbgoioblock.png)
Indicators of Compromise (IOCs)
- several subdomains of mdbgo[.]io
- xxx-three-theta.vercel[.]app
- client1.inftrimool[.]xyz
- psee[.]io
- veluntra-technology-productivity-boost-cold-pine-8f29.ellenplum9.workers[.]dev
- lotusbridge.ru[.]com
- shain-log4rtf.surge[.]sh
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
